For some scenarios, it may be usefull to set up the Linux login to work with Zentyal's Users and Groups (Samba4).
The two main reasons to configure this are:
- Being able to log in with any domain user into any host machine, without granting root privileges.
- Automatically acquiring the main Kerberos ticket (TGT), which
can be then used to transparently access other services in the domain
without prompting for user credentials.
Zentyal
5.0 and Ubuntu
16.04 will be used for this example.
Your Linux client should be able to access Zentyal through the LAN network, Zentyal has to be your default DNS server.
For this example, you will have an example Users domain provisioned, a domain administrator and an example user
Install the required packages on the linux client:
sudo apt-get install sssd heimdal-clients msktutil libnss-sss libpam-sss
You can leave the default Kerberos realm blank, it will be configured later.
As the superuser, edit the file
/etc/krb5.conf and write the following lines, deleting the rest of
the file:
[libdefaults]
default_realm = ZENTYAL-DOMAIN.LAN
rdns = no
dns_lookup_kdc = true
dns_lookup_realm = false
Pay attention to the indentation, there is a
for the parameters inside the block.
Replace the default_realm parameter with your domain, all capital
letters. Pay attention to the capitalization for all the commands in
this document, it is significant.
Open the LDAP port in Zentyal's firewall, section
Internal networks to Zentyal
As the superuser, edit the file
/etc/hosts to configure the FQDN of this host:
127.0.0.1 localhost
127.0.1.1 lubuntu.zentyal-domain.lan lubuntu
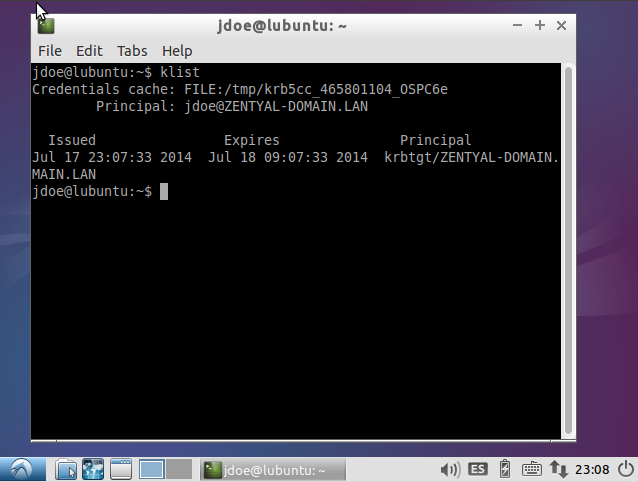
As the regular user, get the Kerberos ticket of the domain admin:
user@lubuntu:~$ kinit Administrator
Administrator@ZENTYAL-DOMAIN.LAN's Password:
user@lubuntu:~$ klist
Credentials cache: FILE:/tmp/krb5cc_1001
Principal: Administrator@ZENTYAL-DOMAIN.LAN
Issued Expires Principal
Jul 17 22:30:04 2014 Jul 18 08:29:53 2014 krbtgt/ZENTYAL-DOMAIN.LAN@ZENTYAL-DOMAIN.LAN
You will now generate the Kerberos principals for this host, replace
the host names for the client and the server, and again, pay attention
to the capitalization:
user@lubuntu:~$ msktutil -N -c -b 'CN=COMPUTERS' -s HOST/lubuntu.zentyal-domain.lan -k test.keytab --computer-name LUBUNTU --upn LUBUNTU$ --server zentyal.zentyal-domain.lan --user-creds-only --verbose
user@lubuntu:~$ msktutil -N -c -b 'CN=COMPUTERS' -s HOST/lubuntu -k test.keytab --computer-name LUBUNTU --upn LUBUNTU$ --server zentyal.zentyal-domain.lan --user-creds-only --verbose
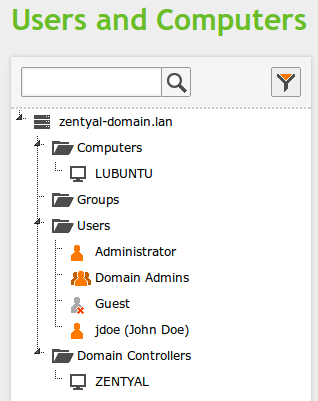
Now, you should be able to see your host name on Zentyal's LDAP tree:
destroy the Kerberos ticket
user@lubuntu:~$ kdestroy
Copy the keytab file to
/etc/sssd:
user@lubuntu:~$ sudo cp test.keytab /etc/sssd/
as a superuser, create the file
/etc/sssd/sssd.conf with the content:
[sssd]
services = nss, pam
config_file_version = 2
domains = zentyal-domain.lan
[nss]
entry_negative_timeout = 0
debug_level = 5
[pam]
debug_level = 5
[domain/zentyal-domain.lan]
debug_level = 10
enumerate = false
id_provider = ad
auth_provider = ad
chpass_provider = ad
access_provider = ad
dyndns_update = false
ad_hostname = zentyal.zentyal-domain.lan
ad_server = zentyal.zentyal-domain.lan
ad_domain = zentyal-domain.lan
ldap_schema = ad
ldap_id_mapping = true
fallback_homedir = /home/%u
default_shell = /bin/bash
ldap_sasl_mech = gssapi
ldap_sasl_authid = LUBUNTU$
krb5_keytab = /etc/sssd/test.keytab
ldap_krb5_init_creds = true
ad_gpo_access_control = disabled
replace domain and host names where necessary, the parameter
krb5_keytab should point to the keytab you created and copied.
Set the correct permissions for the
sssd.conf file:
root@lubuntu:/etc/sssd# sudo chmod 0600 sssd.conf
And restart the SSSD service
root@lubuntu:/etc/sssd# sudo service sssd restart
stop: Unknown instance:
sssd start/running, process 1671
Now, as a superuser, edit the file
/etc/pam.d/common-session and below the line
session required pam_unix.so
Add the line
session required pam_mkhomedir.so skel=/etc/skel umask=0077
Now, you should be able to login as any domain user:
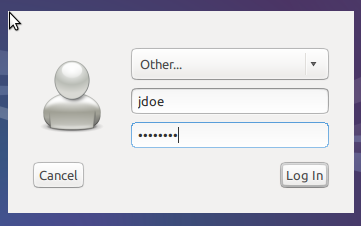
PAM will automatically create the home directory for this user if
needed, and the user will be granted the TGT Kerberos ticket directly
after login in: